Introduction
The digital era has ushered in a wave of technological advancements, with the Internet of Things (IoT) standing at the forefront. This interconnected web of devices offers unprecedented control and data analytics capabilities. Among its many applications, IoT’s integration with access control IoT devices in IoT systems is particularly noteworthy, providing enhanced security and convenience. This blog post will explore the transformative impact of IoT on access control systems.
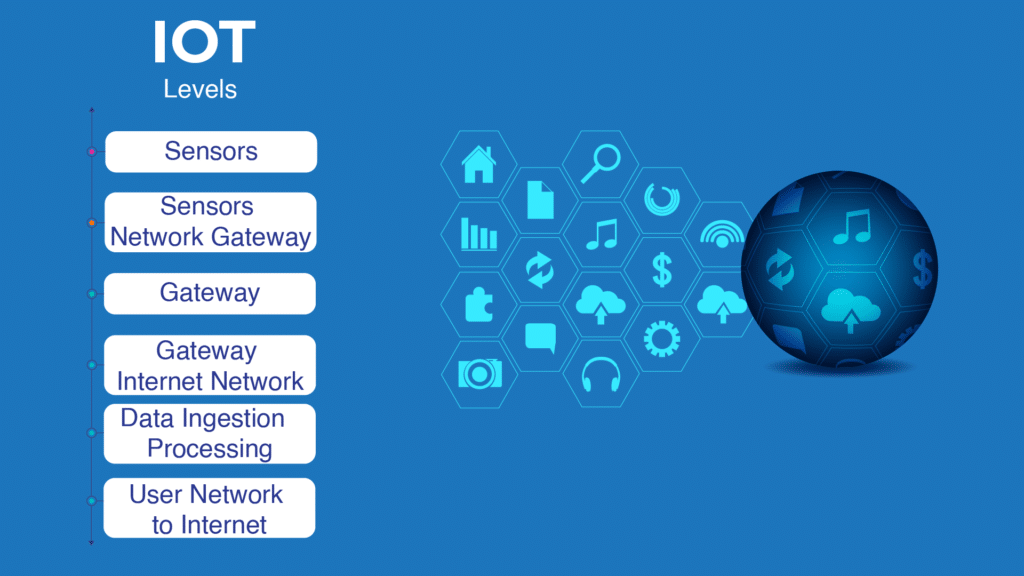
What Is IoT?
The Internet of Things, or IoT, is a technical idea that connects various objects that may be used to turn on and off the web, employ automated processes and software, and enable smart living.
The Internet of Things (IoT) is an innovation that is revolutionizing how we run industrial machines, move and use transportation, and arrange our lives at home and work. About smartphones and wearables, anything can be a part of the Internet of Things, including people.
What is Access Control In IoT?
Access control in IoT levels is a set of permissions that define who can access and what can be done with a connected camera or any other Internet of Things device. This is where Access Control Management Software comes into play. A camera, a user, and the proper access level are defined for each item in an Access Control List (ACL).
What are the Access Controls of IoT devices?
This is the actual hardware that an access control system requires to impose these regulations is called an access control IoT device. Locks, card readers, biometric devices, and controls are a few examples.
The Importance of Access Control in IoT
Access control systems are essential for protecting assets, whether they’re physical buildings or sensitive data. The advent of IoT has elevated these systems, enabling them to communicate with a network of devices for improved security measures. Implementing Privileged Access Management is crucial in IoT environments to ensure that only authorized users can access high-level controls and sensitive functions, thereby reducing the risk of unauthorized access. The logical design of IoT allows for real-time alerts, detailed access logs, and remote management, ensuring that security personnel can respond promptly to any incidents.
Types of Access Control of IoT Devices
IoT has given rise to a new breed of Access control IoT devices:
- Biometric Systems: These devices offer a high level of security by using unique biological traits for identification. They are particularly useful in high-security areas where traditional keys or codes might be shared or stolen.
- Smart Locks: These locks can be controlled remotely through mobile apps, allowing for convenient access management. They’re ideal for residential and commercial properties where access needs may change frequently.
- RFID Readers: Common in corporate environments, RFID readers provide quick and efficient access control. They can be integrated with other systems like time attendance for multifunctional use.
Benefits of Integrating Access Control with IoT
Combining IoT with access control systems yields several benefits:
- Enhanced Security: With features like encryption and multi-factor authentication, these systems are less susceptible to tampering and unauthorized access.
- Convenience: Users can gain entry without physical keys or remember complex codes, streamlining the access process.
- Scalability: As organizations grow, their security needs can change. IoT-enabled systems can be easily updated or expanded to accommodate these changes.
Also Read - Communication Protocols In IoT | How Do IoT Devices Interact?
Challenges and Considerations
While IoT access control devices offer many advantages, they also come with challenges:
- Network Dependency: These devices rely on network connectivity, which can be a point of vulnerability if not properly secured.
- Privacy Concerns: The collection and storage of data by these devices must be handled carefully to protect individual privacy rights.
Future Trends in Access Control for IoT
The horizon is bright for IoT in access control with trends like:
- AI Integration: Artificial intelligence can analyze access patterns to predict and prevent security breaches before they occur.
- Blockchain Technology: By creating an immutable ledger of access events, blockchain can enhance the integrity and traceability of access control logs.
Benefits of IoT in Access Control
The following are the primary advantages of utilizing an IoT-based security system:
- A very intelligent and fully integrated system
- Available from any location in the globe
- Suitable for both human and automated tasks
- Simple to follow event records
- The ability to set up for various level authorities
A thorough strategy for living a secure existence
The Disadvantages of IoT in Access Control
The following are the primary drawbacks of utilizing an IoT access control system:
- There are still certain security and hacking-related problems.
- Inadequately developed technology
- Difficult and expensive
Advantages & Disadvantages of IoT
Conclusion
IoT-enabled access control devices represent a significant leap forward in security technology. By staying informed about the latest developments and best practices, organizations can leverage these tools to create safer, more efficient environments.
Access Control of IoT Device - FAQs
What is IoT access control?
Access control in IoT is a set of permissions that define who can access and what can be done with a connected camera, or any other Internet of Things device, is called access control.
What are access control devices?
This is the actual hardware that an access control system requires to impose these regulations is called access control IoT devices. Locks, card readers, biometric devices, and controls are a few examples.
What is ACL for IoT devices?
Access control is a set of permissions for a connected camera (or other IoT device) that govern which users have access and what operations they may execute. A camera, a user, and the corresponding access level are all specified for each item in an Access Control List (ACL).
Why is access control used?
Access control prevents dishonest people or other unauthorized users from stealing sensitive information, including customer information and intellectual property. It also puts web-based dangers at bay and lowers the possibility of employee data leaks
Related Posts
What Are The Functional Blocks of IoT Devices & Their Functionalities?
Internet of Things | IoT Design Methodology And Its Importance