Cyber-attacks are constantly evolving, and companies that focus on managing issues after an attack often end up falling behind. These businesses that only react when an attack occurs may face money loss, reputation harm, and interruptions in workflow. The best and most effective way to reduce risk is to find vulnerabilities before giving cyberattacks a chance to exploit them.
By leveraging monitoring systems for phishing activity, preventative security gap analysis, and empowering security, businesses can drastically minimize the likelihood of cyberattacks. These preventive measures not only prevent thefts but also strengthen lasting cybersecurity measures.
This comprehensive blog will cover five crucial methods for businesses to identify and prevent cyber threats before they worsen their security practices.
1. Performing Continuous Security Evaluation

Among the powerful methods to protect against cyberattacks is continuous monitoring of vulnerabilities under your business’s system and network. Modern cybersecurity solutions like Cyera DSPM support this by uncovering sensitive data across your environment and highlighting exposure points before they lead to incidents.
Those businesses who did not implement robust security measures are more likely to be exploited, and cyber attackers leverage these weak points.
An all-encompassing security evaluation typically involves.
- Identifying Potential Risks – Spot outdated software, misconfigured systems, and vulnerable access control can open the door for attackers.
- Check Security Protocols: This ensures that internal guidelines are up to date and aligned with robust security standards and legal obligations, and IT compliance management frameworks.
- Pretend Attack Scenarios: Evaluate the business’s security guidlines are effective and can defend against potential risks.
These evaluations not only provide clear insights into current security policies but also highlight the areas that need improvement. Without regular monitoring, the security flaws are overlooked until it worsens.
Carefully identifying vulnerabilities through techniques like ethical hacking enables businesses fill the security gaps, not giving attackers a chance to exploit them. Consequently, security audits are the vital components of managing cybersecurity risks. Hence, Evaluations alone are not sufficient— businesses also need to utilise consistent tracking to identify threats in real-time.
2. Execute Ongoing Network Surveillance
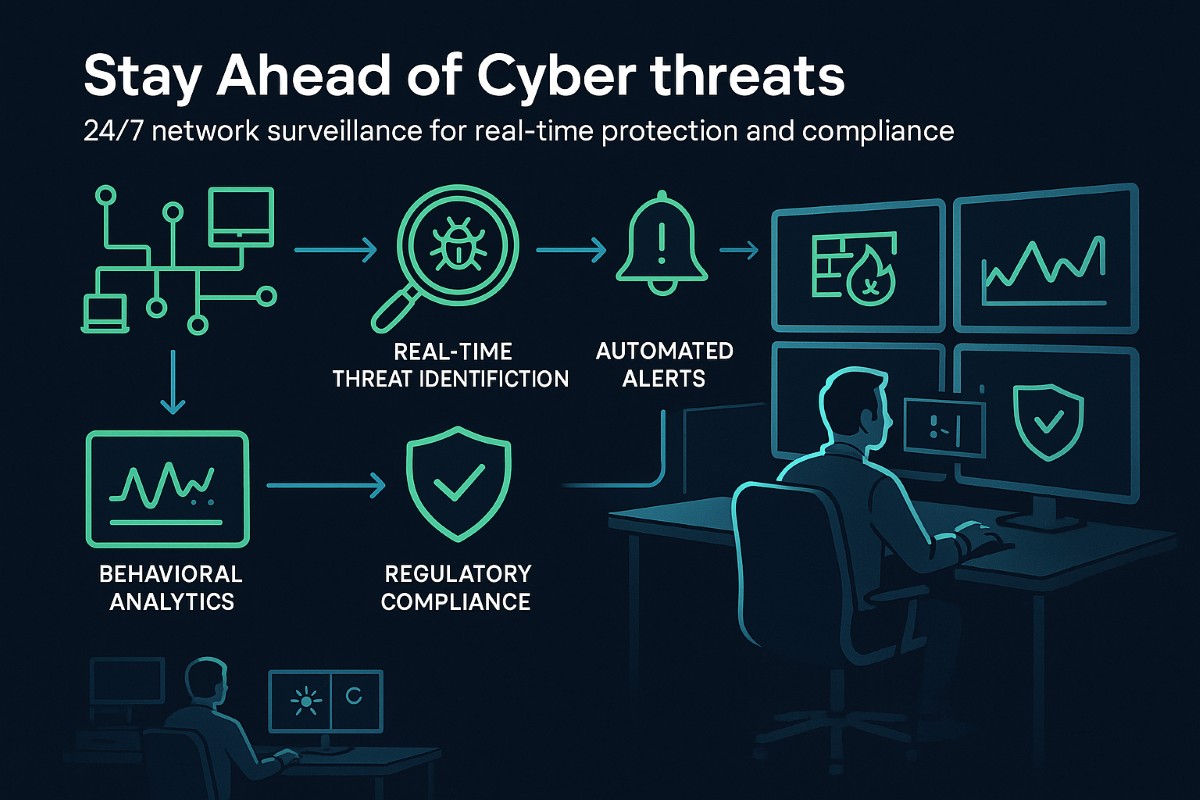
Cyberthreats don’t have a constant time; attacks occur at any moment. Meanwhile, businesses that entirely depend on occasional security practices might miss important warning signals. Here is where continuous network monitoring ensures that potential risks are detected and resolved instantly, minimizing the chance of overlooked breaches.
Core advantages of a continuous monitoring system are:
- Real-time Threat Identification: Detects suspicious activities like unauthorized access attempts or abnormal data exchanges before things get out of control.
- Automated Notifications and Responses: Robust security tools can early detect and alert teams to suspicious activities and, in worse cases, automatically block harmful actions.
- Regulatory Compliance and Risk Management – Continuous monitoring ensures businesses to meet compliance with regulations by keeping track overly critical data and system privileges.
Advanced security solutions use behavioral analytics and threat intelligence to distinguish normal business activity from potential security incidents. By analyzing network traffic patterns and system behaviors, businesses can detect threats before they cause damage.
While monitoring strengthens a company’s defense, it works best when combined with proactive security testing. This brings us to the next critical step: using simulated cyberattacks to identify weaknesses before real attackers do.
3. Using Simulated Attacks to Test Defenses
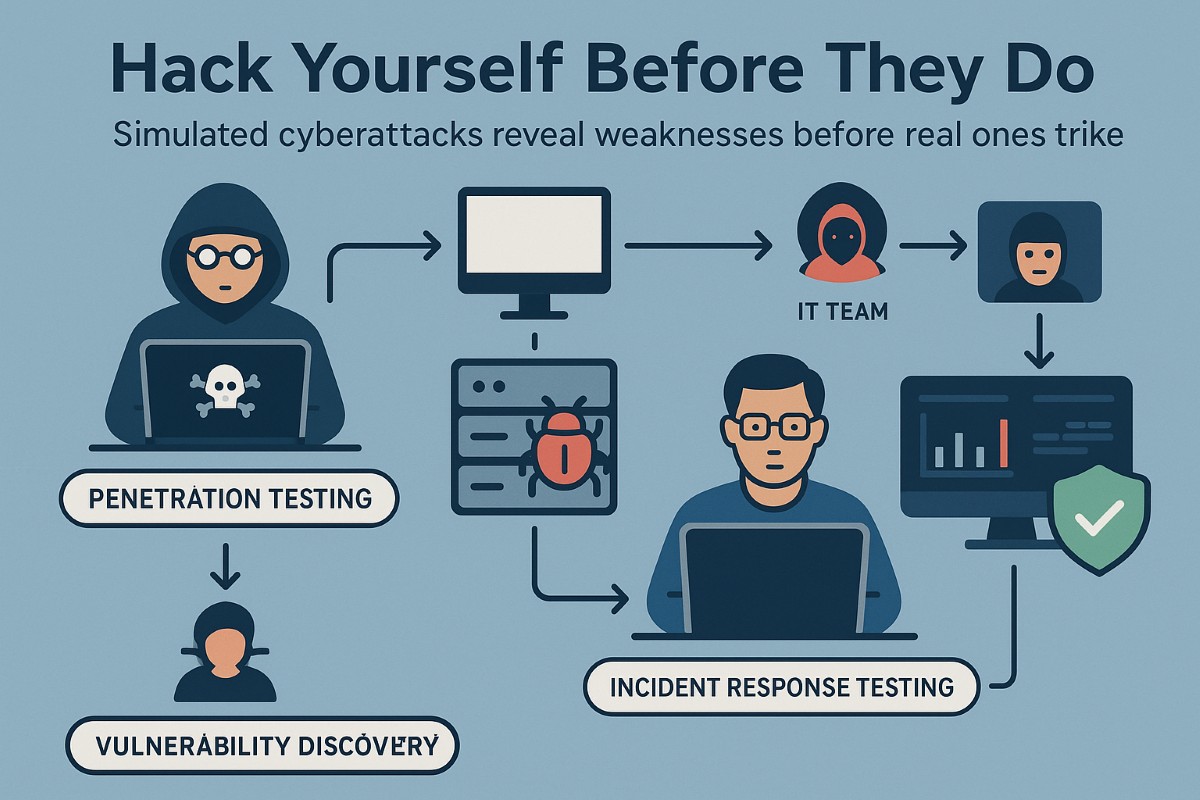
Even with strong security measures in place, businesses can’t be certain of their defenses unless they’re tested under real-world conditions. Simulated cyberattacks, such as penetration testing and red team exercises, allow organizations to evaluate their security posture by mimicking the tactics used by real attackers.
Why Simulated Attacks Are Effective:
- Identifying exploitable vulnerabilities – Ethical hackers attempt to breach systems, uncovering weaknesses before malicious actors do.
- Testing incident response readiness – Simulated attacks reveal how well internal teams detect and respond to security threats.
- Validating security investments – Businesses can assess whether their existing security tools and protocols are effective or need improvement.
Organizations that incorporate ethical hacking as part of their security strategy gain valuable insights into their risk exposure. By learning from controlled attack scenarios, businesses can reinforce weak points before an actual cyberattack occurs.
However, detecting threats is only part of the equation—businesses must also educate their teams to prevent human error from becoming a security risk. This leads us to the next step: ensuring employees are properly trained in cybersecurity awareness.
4. Training Employees to Recognize Cyber Threats
Even the most advanced cybersecurity measures can be undone by human error. Employees are often the first line of defense against cyber threats, but without proper training, they can also be the weakest link. Phishing scams, weak passwords, and accidental data leaks are common ways attackers gain access to systems. Businesses that prioritize cybersecurity awareness training can significantly reduce these risks.
Key Areas of Employee Training:
- Recognizing phishing and social engineering attacks – Employees should be trained to identify suspicious emails, links, and phone calls designed to steal credentials.
- Using strong authentication methods – Encouraging multi-factor authentication (MFA) and secure password practices prevents unauthorized access.
- Following data protection protocols – Employees handling sensitive information should understand how to store, share, and dispose of data securely.
Regular training sessions and simulated phishing exercises help employees stay vigilant. When businesses combine cybersecurity education with proactive security measures, they create a well-rounded defense against cyber threats.
However, cyber threats are constantly evolving, and staying ahead requires ongoing effort. This brings us to the final step: keeping security strategies up to date with the latest threat intelligence.
5. Staying Ahead with Threat Intelligence and Updates
Cyber threats are constantly evolving, and businesses that fail to adapt risk falling behind. Attackers are always developing new tactics to exploit vulnerabilities, making it essential for organizations to stay informed and update their security strategies accordingly.
How Threat Intelligence Strengthens Cybersecurity:
- Identifies emerging attack methods – Threat intelligence helps businesses anticipate new cyber threats before they become widespread.
- Provides real-time security insights – Monitoring global attack trends allows organizations to adjust their defenses proactively.
- Enhances decision-making – Security teams can prioritize vulnerabilities based on the latest attack data, ensuring the most critical risks are addressed first.
In addition to leveraging threat intelligence, businesses must also ensure that their software, security tools, and internal policies remain up to date. Regular software updates and patch management are critical in preventing attackers from exploiting outdated systems.
By staying ahead of threats and continuously improving security practices, businesses can significantly reduce their risk exposure. Combining these efforts with ongoing security assessments, employee training, and proactive monitoring creates a strong, adaptable defense against cyber threats.
With these strategies in place, businesses can shift from a reactive approach to a proactive cybersecurity mindset, ensuring long-term protection and resilience.
Conclusion
Cyber threats are not a matter of if, but when. Businesses that wait for an attack to happen before taking action often find themselves facing costly downtime, financial losses, and reputational damage. The key to effective cybersecurity is identifying threats before they strike and taking proactive measures to minimize risk.
By implementing regular security assessments, continuous monitoring, simulated attacks, employee training, and threat intelligence, businesses can build a strong defense against evolving cyber risks. These steps not only protect sensitive data and critical systems but also ensure operational stability and customer trust.








