Authentication security has never been more critical. You are responsible for various things as a developer. These range from safeguarding user data to ensuring only legitimate users gain access to systems. Essentially, it includes everything that helps protect sensitive information from unauthorized access.
Unfortunately, cyberattacks are on the rise these days. Therefore, it is essential for developers to understand the core principles of authentication and how to implement the best practices, whether you’re using Auth0, another commercial solution, or a custom-built system.. It is no longer optional—it's a necessity.
But why is authentication security so crucial today? The answer is simple: as more of our personal and professional lives go digital, the risk of data breaches and unauthorized access grows. Hence, secure authentication is the first line of defense against these risks.
So, what should every developer know about authentication security? Let us explore below.
Why Strong Passwords Are Still Relevant
In the age of biometrics and sophisticated authentication methods, it's easy to overlook the power of a strong, unique password. But do not be fooled; passwords still secure accounts.
Therefore, you must follow best practices for setting up a password. It includes the use of a mix of uppercase and lowercase letters, numbers, and symbols. Simply put, longer passwords are harder to crack. It is also important to use unique passwords for different sites and services.
Plus, strong passwords are important, and luckily, password managers make it easy to store and manage them securely. Additionally, multi-factor authentication (MFA) adds an extra layer of protection, which we will discuss shortly.
1. The Importance of Token-Based Authentication with Auth0
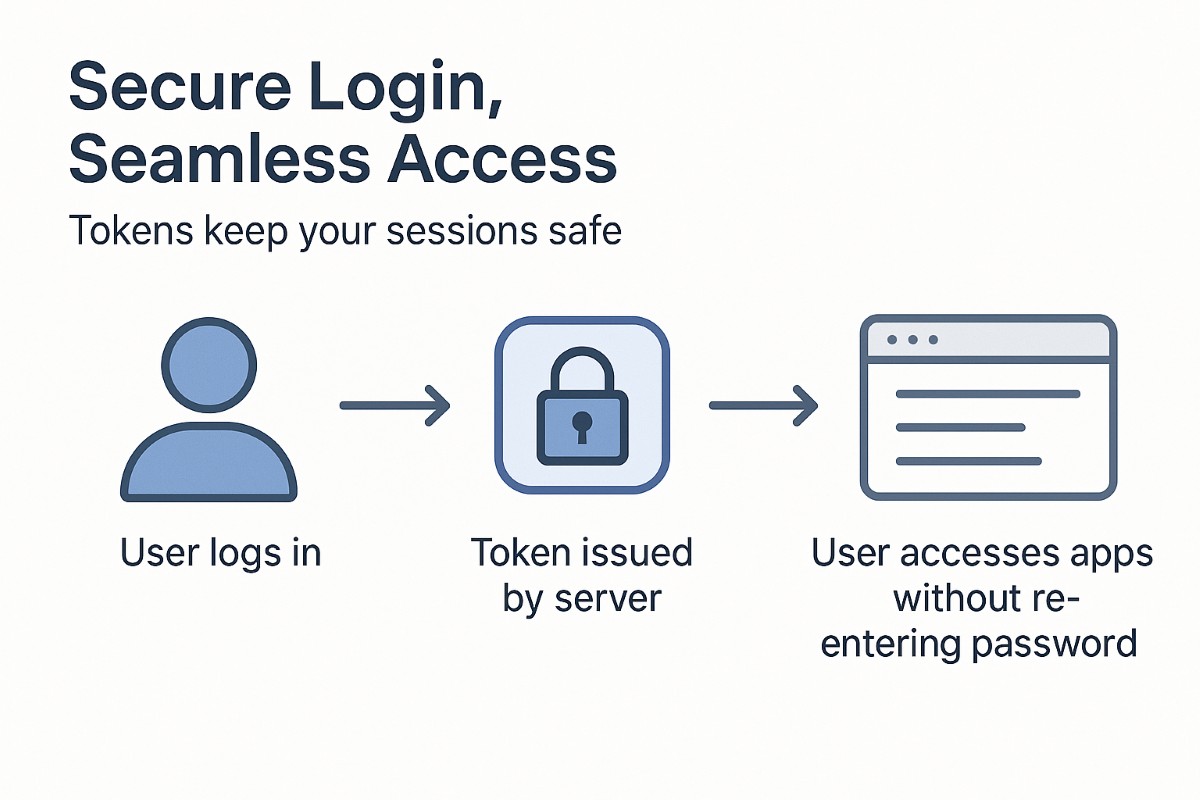
Token-based authentication has become a popular method for securing user sessions. It means that platforms do not repeatedly ask for usernames and passwords. Instead, they issue tokens to users after authentication. These tokens help in maintaining an active session without requiring login credentials with every request.
They offer several advantages. For example, they help in scalability and the ability to handle distributed applications. Luckily, there are platforms that assist in token-based authentication. Lately, Auth0 has traditionally been a popular solution for managing tokens.
However, many developers are now exploring more cost-effective options due to Auth0 pricing. For example, platforms like SuperTokens are gaining popularity as an alternative. It offers robust token-based authentication at a lower price point. The need for affordable, scalable, and secure authentication solutions drives the shift.
In simple words, using the right platform ensures a smoother, more efficient token-based authentication process. It helps maintain secure sessions and provides users with a seamless experience.
2. The Role of Multi-Factor Authentication (MFA)
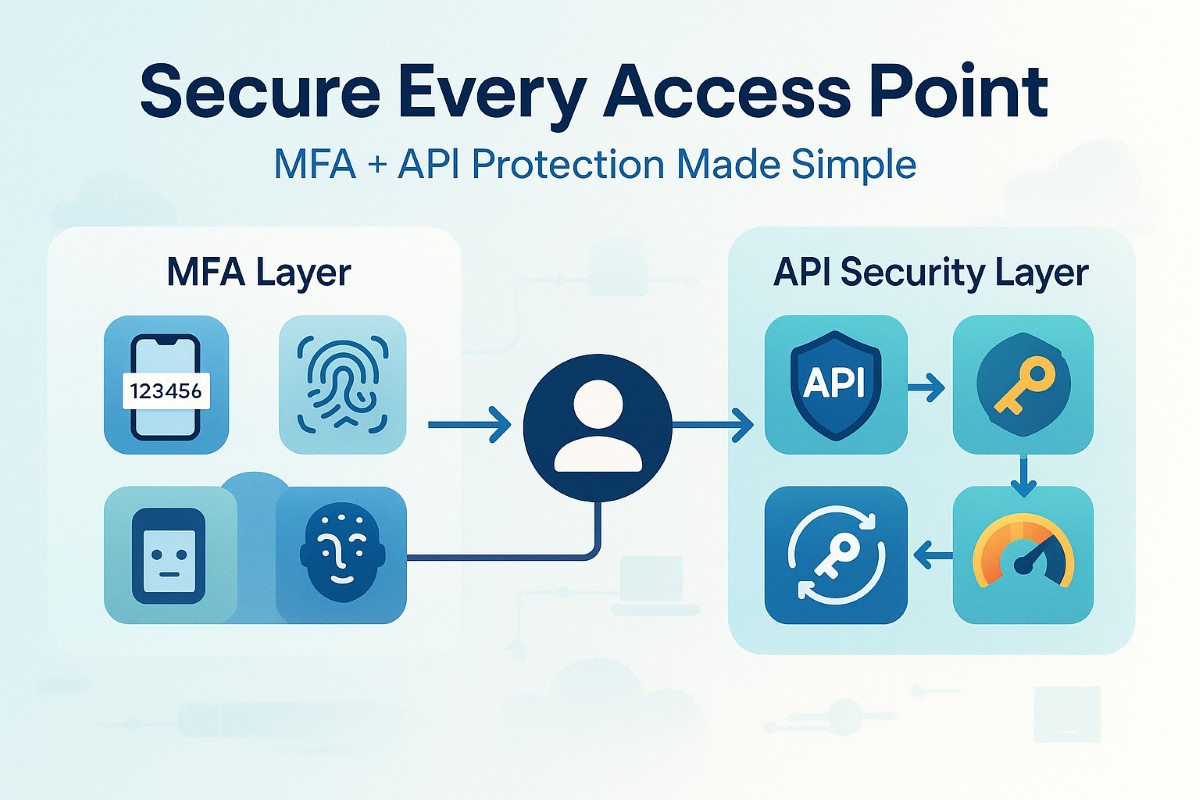
Multi-factor authentication (MFA) is no longer optional. It is essential for enhancing security. MFA adds a second layer of protection by requiring more than just a password to verify a user's identity. Auth0 also provides built-in MFA capabilities, allowing developers to enable this extra layer of protection with minimal setup. It could be a one-time code sent to their phone, a fingerprint scan, or a facial recognition scan.
It drastically reduces the risk of unauthorized access, especially if credentials are compromised. It is one of the easiest ways to bolster security, and most modern platforms implement it.
It is safe to say that MFA is a standard on every platform, from social media sites to online banking, and is not an exception.
Securing APIs and Third-Party Integrations
Today, the digital landscape is interconnected. Therefore, many applications rely on APIs and third-party integrations. These tools are essential for providing features and services. That said, they also present security risks if not properly managed.
Therefore, it is important to use secure authentication protocols, such as OAuth, when integrating APIs. Auth0 can also manage these secure flows, issuing and validating OAuth tokens to keep integrations safe. It helps ensure that access is granted only to authenticated users. Additionally, API keys should never be hardcoded or exposed in client-side code. Rather, you must store them securely and ensure they are rotated regularly.
You should also know about the best practices for API security. These include:
- Use rate limiting to prevent abuse
- Secure API gateways
- Ensure that third-party services comply with industry security standards.
3. Protecting User Data During Authentication
Protecting the user information is of topmost priority, and it starts from authentication itself. Using identity platforms like Auth0 helps enforce encryption and hashing best practices automatically. All the sensitive information, such as passwords and user information, has to be encrypted at each point.
TLS/SSL encryption protocols will secure data in transit, thus ensuring the attacker can no longer tap information flowing from users to servers. Moreover, password hashing algorithms like bcrypt or scrypt will secure your database by making sure that even if the attacker gains access to your database, they cannot easily access plain-text passwords.
Remember: never store plain-text passwords in your database. Always hash passwords before storing them and never transmit sensitive data without encryption.
4. Common Authentication Vulnerabilities and How to Prevent Them
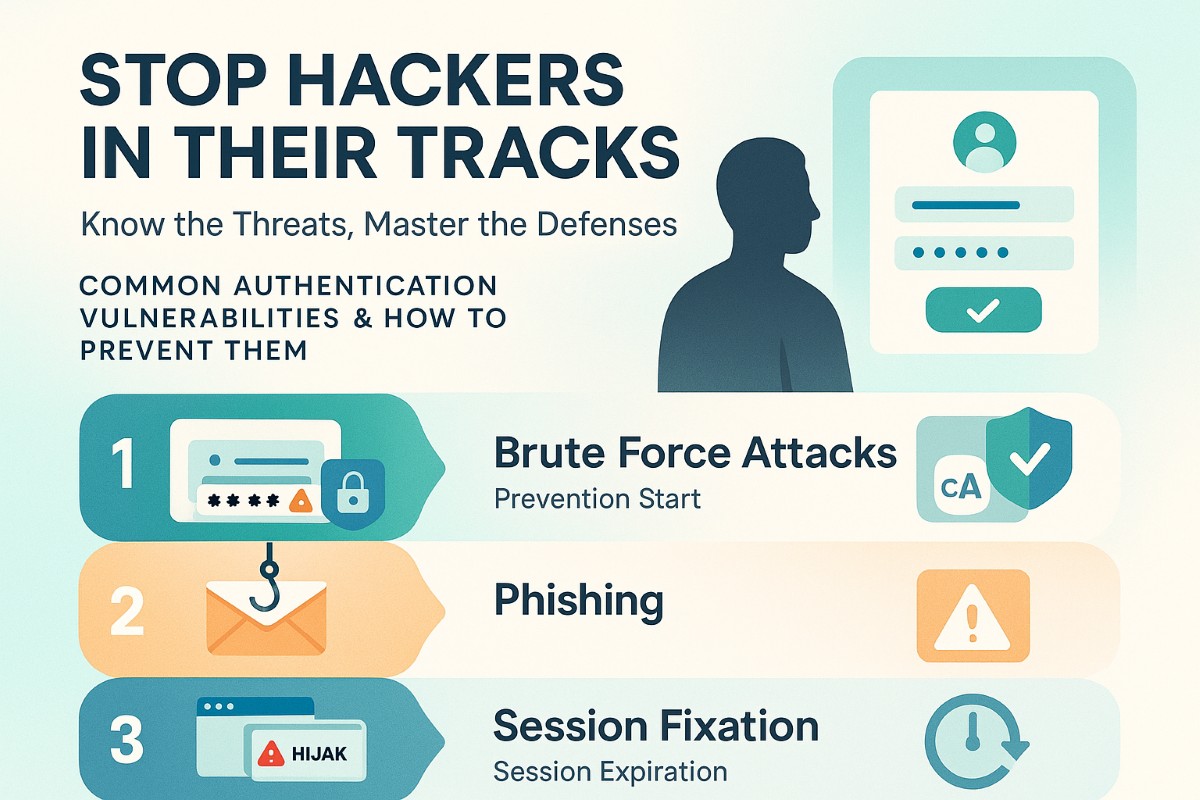
All programmers must be familiar with typical vulnerabilities used to violate authentication security:
- Brute Force Attacks: Attackers can attempt various combinations of passwords to gain entry into accounts. Rate limiting or CAPTCHA can stop this.
- Phishing: Attackers mislead users into providing their credentials. Hence, user education in the identification of phishing is a must.
- Session Fixation: Hijacking of a legitimate session. This risk can be softened by employing proper session management methods, including session expiration and re-authentication.
👉 While preventing brute-force attacks or phishing is essential, systems such as CRMs require additional layers of protection—especially with access controls, encryption, and monitoring. You can explore more detailed CRM-specific cyber-security strategies in this helpful guide: Essential CRM Cyber Security Strategies.
In short, you actually can make your application a whole lot safer if you understand these vulnerabilities and add countermeasures.
Wrapping It All Up
Secure authentication is a cornerstone of any software application. You should know the most important principles and best practices for safeguarding users' data. Plus, make sure only authorized individuals are allowed to access guarded resources. It may be creating robust passwords, using multi-factor authentication, or protecting APIs, but whatever you decide affects the security of your users.
By using the techniques outlined here, you will be capable of writing stronger, safer applications that keep users safe and their data secure. Stakes are high, but with the right tools and knowledge, you can help create a safer internet for all of us. Whether you choose Auth0 or another platform, the goal is the same—secure, seamless authentication for every user.








